1,000,000 trained
cyber security
professional Cyber security jobs
are expected
to increase 37%
through 2022 More than 80%
of U.S. companies
have been hacked Cyber security
spending to Exceed
$1 Trillion
from 2017 to 2021 Cyber security
unfilled jobs are
expected to reach
3.5 million by 2021 You are 600 times
more likely to be hired
as a Cyber Security
professional
Post Graduate Program in
Cyber Security (PGPCS)
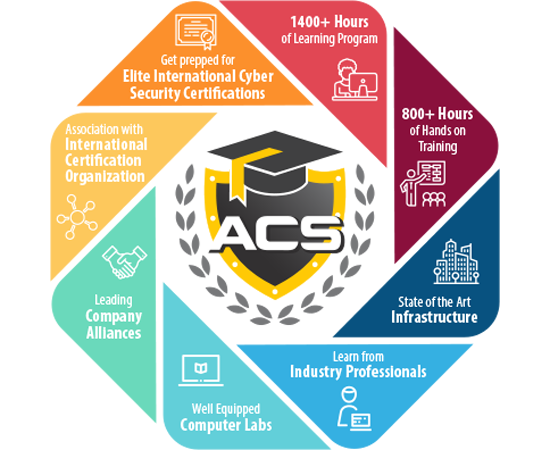
Our Flagship 6 months full-time residential program transforms individuals into cyber security professionals and prepares them for 4 Major International Certifications.
The Post-Graduate Program in Cyber Security (PGPCS) is the flagship programme of Academy of Cyber Sciences.
The course is uniquely designed to offer more training hours in 6 months than most masters and bachelors program offer over 3 yrs. The course through its high-pressure schedule prepares candidates to build the right value systems which are a must for succeeding in technology field. The course challenges traditional methodologies of education and provides a magical shift to one's career by preparing them to meet the changing market needs.
There is no one true path to working in cyber security. People come at it from all angles – math, computer science, engineering, technology, even history or philosophy. Yet all of them share a deep and abiding interest in how technology works. Security gurus say this is critical. You need to know exactly what you’re protecting and the reason things are insecure. The course is targeted towards graduates from any discipline and IT professionals who wish to pursue their career in the fastest growing professional field of Cyber Security.
The course aims to groom the students and enable them to work on current technology scenarios as well as prepare them to keep pace with the changing face of technology.
The entire course syllabus, course ware, teaching methodology and the course delivery have been derived from the rich research and development done by teams and partners of Academy of Cyber Sciences from across the world.
The depth and width of the course is unique in the industry covering a wide spectrum of requirements of the cyber security industry.
PGPCS is a six-month full-time course, consisting of thirteen compulsory modules and a Project, designed to help all those desiring to reach the cutting edge of Information Technology and to contribute in the high potential field of Cyber Security.
PGPCS is best suited for:
- Graduate students of all disciplines
- Professionals desiring to migrate to IT
- Students appearing for the final year of graduation
- The candidates should have 10+2+3 or 10+2+4 years of formal education leading to a degree of a recognized university.
- The candidates who have completed 10+3 years of formal education leading to a Program in Engineering or its equivalent from a recognized body and followed by at least 2 years of additional qualification and/or relevant experience. Sound knowledge of Computer Fundamentals is essential.
- The applicant must also be conversant with Object Oriented Programming concepts and must be proficient with C++ Programming and Data Structures using C++.
- For selection, the candidate must clear the Common Entrance Test, with 60% marks in Technical Section & 70% marks in aptitude section. The detailed syllabus of CET (Common Entrance Test) is given in the PGPCS course brochure.
The total fee of the course is INR 1,44,000/- + Taxes.
The course fee has to be paid in two instalments as per the schedule.
- First instalment is INR 25,000/- + Taxes to be paid by shortlisted candidates at the time of Practical Test after clearing the CET.
- Second instalment is INR 1,19,000/- + Taxes before course start.
FINANCIAL AID
ACS provides Financial Aid to 20 students per batch for the flagship course of PGPCS.
On clearing Common Entrance Test (CET) and receiving offer of admission you may decide to apply for financial aid at finaid@academyofcybersciences.com.
Your application mail should have following –
- An essay on “What Makes Cyber Security a Rewarding Career for You”. The essay should not exceed 400 words or it will be automatically rejected.
- Please mention your CET application form number.
| Operating Systems |
|
| Software Engineering |
|
| Advanced Networking Concepts |
|
| Basic Web Technologies |
|
| Java & Java Scripting |
|
| PHP & XML |
|
| Microsoft .Net Framework |
|
| Database Technologies RDBMS, SQL / PLSQL |
|
| Mobile Computing |
|
| Offensive Security |
|
| Defensive Security |
|
| Incident Response & Forensics |
|
| Cyber Security Management |
|
Please Note: The cyber security landscape is every changing so the course content mentioned above could change by the time you join the course. This is the indicative sample of current ongoing batches.
After completion, of course students will be able to acquire the following skills:
- Appear for CISO and CISSP exams at international levels.
- They can take up position in organizations as CISO in top corporates ranging from Fortune 100 companies to mid-sized corporates Or start their own enterprise to offer these services in high potential field of Cyber Security, Cyber Crime Investigation, Cyber Forensic and Ethical Hacking.
- Would be able to understand use of technologies to access and interpret information effectively. They would be able to understand the threats and create their own methodologies to secure and respond to threats.
- Build an aptitude for field of computers and related areas.
- Use communication technologies competently.
- Understand the multi-tier architecture of web-based enterprise applications using - Enterprise JavaBeans, Integrate Servlets, JSPs with EJB and Databases in J2EE application, .Net architecture, and able to maintain the applications.
Preparatory course for PGPCS
For those who do not come from programming background can still pursue a career in Cyber Security with a 3 months part time preparatory course for cracking CET. This program will train you on C / C++ and other analytical skills which are essential for PGPCS.
How to prepare for the Common Entrance Test for PGPCS
The CET will test the candidate's knowledge of Object Oriented Concepts, independent of any specific language, C++ Programming capabilities, Data Structures using C++ as well as candidate’s aptitude. The candidate must possess good knowledge of C++ Programming Language in terms of its syntax and especially its object oriented features and their appropriate use.
The candidate should carefully study the books prescribed herein. However, programming ability cannot be developed by merely reading language constructs from the book. It is absolutely necessary to actually write one's own codes in C++ Language and implement at least 100 good C++ Programs on a computer. These programs should be of increasing complexity and should exploit appropriate constructs and Object Oriented features of C++ and use Data Structures using C++ extensively. Candidates should solve all the problems given in the prescribed books. It is also necessary to study good codes written by experts as given in the CD accompanying the book.
The applicant should also practice the use of good features of the language, modularize his/her codes, put suitable comments to improve readability of the codes, make extensive use of library routines and format the programs to express the logical flow clearly. The candidate should note that the rigorous programming practice prescribed above is not only required to succeed in the Technical Theory section of the Common Entrance Test to be followed by Technical Practical section, but also required to learn various modules of PGPCS with rapid pace. The rigorous programming practice is in fact the most important prerequisite to undertake the PGPCS Course and successful career in the IT industry thereafter. The motivation of this text is, therefore, to ensure your development in the right direction.
Object Oriented Concepts
(25% Weightage)
Understanding of the object-oriented concepts, such as Classes and Objects, Inheritance, Polymorphism, Abstract Classes and Re-usability, etc.
C++ Programming
(50% Weightage)
Datatypes, Variables & Constants, Operators, Associativity and Precedence of Operators, Input-Output, Control Constructs, Using Functions from Libraries, Pre-processor Directives, Programmer Defined Functions, Scope and Lifetime of Variables, Recursion, Parameter passing by reference and by value, Classes and Objects, Member Variables and Member Functions, Constructors and Destructors, Function and Operator Overloading, Inheritance, In-line Member Functions, Private, Public and Protected.
Data Structures using C++
(25% Weightage)
Arrays, Stacks, Queues, Linked Lists (Singly, Doubly, Circular), Trees, Threaded trees, Graphs, Sorting (Bubble, Quick, Heap, Merge)
1. C++ Programming Bible
Al Stevens and Clayton Walnum
(IDG Books India)
2. The Object-Oriented Thought Process
Matt Weisfeld
(Techmedia)
3. Data Structures, Algorithms and Applications in C++
Sartaj Sahni
(Tata McGraw Hill Publishing Co.)
Admissions
Enrolling in ACS is simple, quick and flexible. Following enrollment form is to officially connect you with our experts who treat you and guide you as a young professional rather than student.
Academy of Cyber Sciences (ACS) application form for the Common Entrance Test (CET), the course brochure and study material can be procured by paying a registration fee of INR 1500/- (Rupees Fifteen Hundred only). The registration and payment can be done online. The application form duly filled-in is to be submitted online at ACS Portal.
The Selection Process leading to confirmed admission shall unfold in two stages as described below:
Stage I: Common Entrance Test (CET)
The CET is online test consists of objective type multiple choice questions with three sections, Technical Theory, Technical Practical & Aptitude.
On the basis of performance in the CET, the candidates shall be shortlisted in the order of merit. The shortlisted candidate shall be required to undertake Stage II of the selection process, subject to successful clearance of which, the candidate shall be offered admission.
(For more information on conduct of CET, please see the instruction sheet given along with the application form.)
Stage II: Interview
The interview stage consists technical interview based on the syllabus of CET and a personal interview of the candidate. During the interview, the candidate can seek more information about the center and the facilities available there for undergoing PGPCS. After the candidate successfully completes both the stages of the selection process, he/she shall be given a letter of Offer of Admission to PGPCS.
The Technical Theory section will cover theoretical concepts of Object Oriented Concepts, C++ Programming and Data Structures using C++.
This shall be immediately followed by a Technical Practical section which shall test the practical knowledge of the candidate on the same topics.
The Aptitude Test shall be modelled on the pattern of GRE/GMAT. It will consist of question in English, Mathematical ability, Reasoning and Problem Solving ability.
onlline here.
| Course Marketing Start | Thursday, July 13, 2017 |
| Forms Sale Start | Thursday, July 13, 2017 |
| Forms Sale End | |
| Last Date of Submission of Forms | Friday, August 04, 2017 |
| Dates of CET | Saturday, August 12, 2017 Sunday, August 13, 2017 |
| Result of CET with Waitlist | Friday, August 18, 2017 |
| PI Date - 1st Installment Payment | Friday, August 25, 2017 |
| Final Admissions List | Monday, August 28, 2017 |
| Wait List Confirmation | |
| Last Date of Payment of Entire Fees | |
| Course Start Date |
About Us
Academy of Cyber Sciences (ACS) is part of 20+ years old Education & Training division of Gateway Group of Companies.
ACS focuses on providing top of the line skill based, marked-to-market training to aspiring candidates who wish to build their career in the ever changing, exciting and thrilling field of Information Technology.
ACS addresses the rising demand for Global Cyber Security professionals. ACS fills this gap of skilled resources by means of highly specialized, tailored and focused training programs taught by industry leaders who train future cyber security experts on various critical aspects of the cyber security.
Our programs are designed to rigorously create, innovate and test your knowledge on the core skills required to become a successful cyber security expert. Completion of our programs you will earn industry acknowledged ACS certification that will act as a valuable asset in your professional journey and propel your career to great heights.
Let's Connect
Contact Information
- Academy of Cyber Sciences,
A 92, Corporate House,
Bodak Dev,
Ahmedabad - 380054 - +91 79 26852554
- +91 79 26858591
- inquire@academyofcybersciences.com
- www.academyofcybersciences.com
- academyofcybersciences